Identity theft occurs when someone uses your identity in a crime or fraudulent act. Ad Have Full Control of Your Credit Activity.

Tips And Advice To Prevent Identity Theft Happening To You Europol
The identity thief may use your information to apply for credit file.
. Identity Theft Investigation More than 5000 000 people nationwide will become identity theft victims in the year 2000 an increase of more than 450 000 annual cases over the last 5 years. Ad Guard Against Breaches of Lost or Stolen Credentials with Password Protection. Be Safe from Fraudulent Transactions Loans.
Online organisations commonly use electronic commerce approaches. Trusteer Pinpoint Platform Conducts Multi-Layered Assessments to Authenticate Users. Ad Your Digital Financial Identity Face Constant Risks.
These techniques are listed under three headings. Protect Your Family with the Most Comprehensive Identity Theft Protection Available Today. Ad Learn How Digital Identity Trust Works to Authenticate Users and Detect Fraud Seamlessly.
Identity theft has swiftly become a serious issue for victims police and prosecutors and is a problem that is requiring an increased commitment of resources by private enterprise. Join a Plan Today Starting 899. With the growth of technology protecting your personal information has never been more important.
Other types of identity theft. Ad Best Identity Theft Protection Services 2022. E xamining identity theft suspects requires systematic methodical techniques designed to yield evidence for possible prosecution.
See our ID Protection Reviews Find Who Is Rated 1. Online ID theft techniques investigation and response 77. As technology advances so do the techniques used by identity thieves.
Trusteer Pinpoint Platform Conducts Multi-Layered Assessments to Authenticate Users. This paper presents an evaluation of the. Dont Be That One.
It can happen to anyonebut there are steps you can take to protect yourself and to recover if it happens to. If an identity theft suspect has been arrested request. The threat of identity theft is on the rise.
Identity ID theft happens when someone steals your personal information to commit fraud. And 3 social engineering. However these have some limitations in the m-commerce.
Fraudsters use a variety of techniques to acquire a victims card number. Identity Theft happens to 1 Out of 4. Strategies and Techniques Page 3 When a non-union employer or its agent security officer human resource representative supervisor or manager etc conducts.
The University of Glamorgan and is currently working towards a PhD in Data. Identity Guard is Here To Help You. Improve Visibility and Control Access with Adaptive Policies Based on Contextual Factors.
Identity theft since it may occur only once and be discovered quickly by the credit card issuing company often before even the individual card holder knows it. Mining of Intrusion Detection Systems. Examples of how stolen personal information can be used to.
Compare Identity Theft Protection Reviews. Ad Learn How Digital Identity Trust Works to Authenticate Users and Detect Fraud Seamlessly. Get Protection from Identity Theft.

Cyber Crime Investigation Making A Safer Internet Space

Pdf Online Id Theft Techniques Investigation And Response
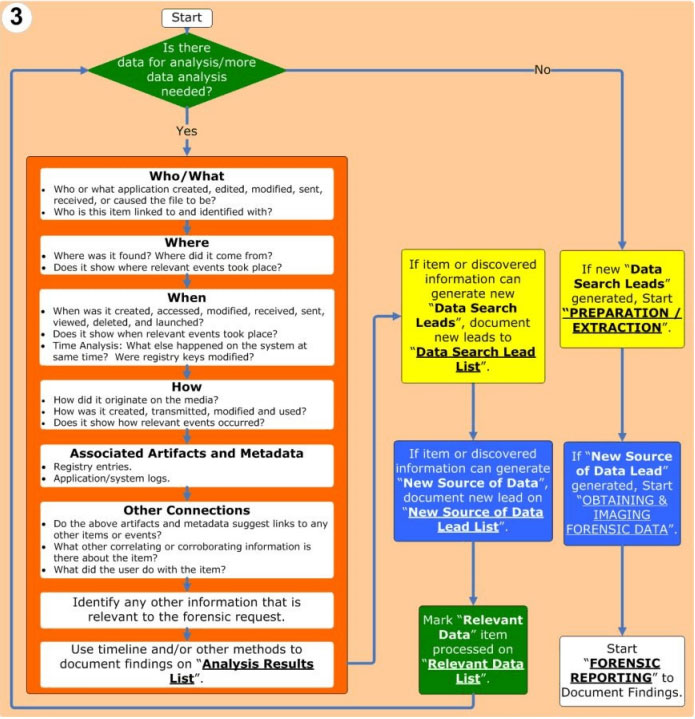
Computer Forensics Digital Forensic Analysis Methodology



0 comments
Post a Comment